What do You have in Your Autopilot setup?

This post is a result of a few weeks of trial and error testing and re-testing and re-running devices through the whole deployment process over and over again. The scenario I am presenting uses pre-provisioning, so that the user phase is kept fairly short.
I'd love to hear about your challenges, experiences, and the tricks you've used to overcome them!
The Goal
- Get the device as close as possible to what a ConfigMgr staged device would look like (I know... I am old)
- Use pre-provisioning so that users don't have to wait too much
- Install the same apps, settings, that you would with ConfigMgr
- Have the device install updates, and get the 'GPOs' - well, configuration profiles
NOTE: there are some settings in a few Configuration Profiles that if you happen to play with, you might just break the user experience, Device Lock policies especially prone to do so. It's best to apply them to the users, rather than to the devices.
Community has worked tirelessly to make things more fool-proof and smooth and there are excellent additions to standard apps. I'll refer to them below.
Pre-provisioning can be performed by the vendor or by field support/service desk teams.
The Flow
I use an OSDCloud USB stick (will make a post about OSDCloud later). This installs the latest Windows 10/11 and injects the OEM drivers directly from the vendor (e.g. Dell, HP, Lenovo...). The whole process takes about EIGHT (yes, 8) minutes (on a fairly modern device with NVMe disk)
At the time of writing I am using Windows 11 23H2.
The Windows image available from Microsoft is typically a few months old. Cumulative updates, Defender's updates, Edge, etc, all is out of date. I'd say it's best practice to have everything patched, before you 'hand over' the device to a user - be the handover happen in person or just virtually, when the user is finally allowed to login.
- Windows 10/11
- Driver pack from the OEM (this is pre-installed by OSDCloud)
- Update Windows
- Update Edge
- Latest Office
- Latest Teams
- Other Apps
The ESP I use is set to block the login until all required apps are installed. While this takes a little longer and many of you would only use a few 'blocking apps', I feel that this way the user can be sure that once logged on, all the 'usual' apps are there and ready.
The Main Ingredients
According to my latest info the only way to control the order of apps during Autopilot Device phase is to make them dependent on each other. That way the chain is worked out by the Intune Management Extension, and it will force to start based on the chain. I was brave enough not to set any dependencies, so far this worked fine.
- Michael Niehaus' script UpdateOS to run Windows Update
While this takes quite a bit of time, it ensures that all updates are installed during Device Phase. .Net updates, Defender, and Cumulative Update for Windows itself. Highly recommended!
- Rudy Ooms' script to fix the activation of Windows 11
This is required, as without it there's a high change that your devices will not get activated and switch SKUs to Enterprise.
- Update Edge during Autopilot
I can't find the source, but it's a single line of PowerShell code that I've wrapped in PSADT for better traceability and logging:
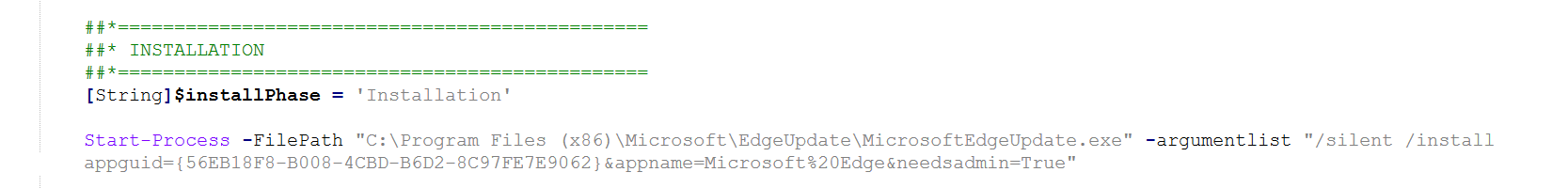
Start-Process -FilePath "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" -argumentlist "/silent /install appguid={56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}&appname=Microsoft%20Edge&needsadmin=True"(Please mind the word wrap if you copy this)
- Office - latest of the Enterprise Monthly Channel
In an earlier post I talked about ways to deploy Office. I use a 32-bit package for Autopilot, supported by two additional packages. These allow the user to freely switch back and forth between the architectures from Company Portal. My Office deployments all use Microsoft's Content Delivery Network, so the packages stored in Intune are quite small.
- Company Portal
If you only select a few blocking apps and forget to add Company Portal, users may complain about not being able to install additional apps after the first login. When building user experience, this is something to keep in mind.
- Start Menu to the left
Having discussed this with a few Workplace gurus, I hear both pros and cons regarding where to orient the Start Menu. I feel that users coming from Windows 10 would naturally expect the Start Menu to appear on the left side of the dock.
It's your choice, but I decided to move it to the left for all users, allowing them to change it later if desired.
NOTE: if you set this via a Configuration Profile from Intune, it means that users won't be able to change this setting. (or at least I could not find a way to do it - Config Profiles don't seem to have the 'apply once and do not reapply' settings similarly to a GPO... as always: tips are very welcome!)
What I ended up doing is adjusting the default user's registry with a script. This works well and users are able to move the Start Menu to the center:
It's in PSADT's Installation section - adjust logging to your liking, by default, it goes to c:\Windows\Logs\WORKSPACE folder:
##*===============================================
##* INSTALLATION
##*===============================================
[String]$installPhase = 'Installation'
$iswin11 = ([environment]::OSVersion.Version.ToString() -match "10.0.22")
if ($iswin11){
& REG LOAD HKLM\DEFUSRPROFILE C:\users\default\NTUSER.DAT
Push-Location 'HKLM:\DEFUSRPROFILE\Software\Microsoft\Windows\CurrentVersion\Explorer'
if (!(Test-Path Advanced)){
Write-Warning "Advanced key is missing"
New-Item Advanced
}
New-ItemProperty -Path .\Advanced -Name TaskbarAl -Value 0 -PropertyType DWORD -Force
Pop-Location
$unloaded = $false
$try = 0
while (!$unloaded -and ($try -le 5)){
[gc]::Collect()
& REG UNLOAD HKLM\DEFUSRPROFILE
$unloaded = $?
$try += 1
}
if (!$unloaded){
Write-Warning "Cannot unload reg key, manual dismount required"
}
$f = "c:\windows\Logs\WOKRPLACE"
$WOKRPLACE = Test-Path $f
if (-not $WOKRPLACE){
New-Item -ItemType Directory -Path "c:\windows\Logs" -Name "WOKRPLACE"
}
New-Item -Path 'c:\windows\Logs\WOKRPLACE' -ItemType File -Name 'Win11StartMenu.log'
Add-Content -Path 'c:\windows\Logs\WOKRPLACE\Win11StartMenu.log' -Value "Windows 11 Start menu was switched to the left"
}else{
$f = "c:\windows\Logs\WOKRPLACE"
$WOKRPLACE = Test-Path $f
if (-not $WOKRPLACE){
New-Item -ItemType Directory -Path "c:\windows\Logs" -Name "WOKRPLACE"
}
New-Item -Path 'c:\windows\Logs\WOKRPLACE' -ItemType File -Name 'Win11StartMenu.log'
Add-Content -Path 'c:\windows\Logs\WOKRPLACE\Win11StartMenu.log' -Value "This is not a Windows 11 device, skipping..."
}- New Teams
Microsoft changed Teams completely earlier in 2024 and soon the classic Teams client will be retired and automatically removed. Installing the New Teams is a piece of cake. PSADT as usual:
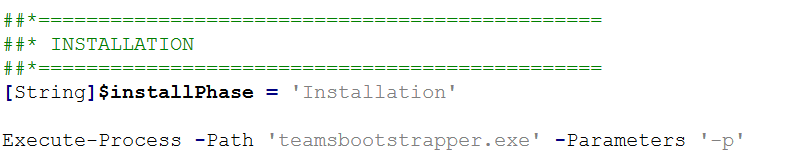
The article here explains everything in detail. Literally the only file you need is teamsbootstrapper.exe executing it with a -p switch. This also does its thing online, so always installs the latest version.
- BIOS settings
My lab has only Dell hardware. For HP and Lenovo the process should be fairly similar. Dell provides a tool called Command Configure featuring a Command Line Toolkit (CCTK). It can easily be scripted. Again, PSADT comes to the rescue, I package CCTK (which by the way is able to run in WinPE! So all settings can be set during a ConfigMgr deployment even before formatting the target disk!). This sets the BIOS password as well as all other settings your heart (and your security team) desires.
Dell recently introduced a tool specifically for Intune. DCECMI - is a long abbreviation I will never remember. It is called Dell Command | Endpoint Configure for Microsoft Intune. Quote from the link:
Custom BIOS configuration profiles can be crafted based on IT environment needs such as Security, Privacy, Performance, etc. and can be assigned to various device groups. The installation is a BIOS configuration based profile. The design of this system is secure and prevents any security gaps for the customers. Microsoft Intune administrative users can now manage the BIOS settings of a fleet of Dell devices.
I will do some testing and hopefully make a post about it soon.
Other Apps
These are small utilities, the exact list will be up to you, for my tests I added a couple of well-known ones:
- Adobe Reader
- 7-zip
- Notepad++
- Dell Command Update for driver updates
Dell's firm stance is that Intune Driver Management is 'not there yet', and they keep actively promoting Dell Command Update as their enterprise grade driver management tool. Furthermore, they only release tested drivers and BIOS updates after monitoring their releases in the wild.
Result
With the settings above, pre-provisioning takes roughly one hour. (The reseal button appears anywhere within 55 minutes up to 1 hour and 5 minutes). I have all the updates, latest Office, Teams, Edge. The device has its BIOS configured and a password set.
The user logon takes about 15 minutes and all apps are there out of the box. Company portal is ready and available. Start Menu is left-aligned.
To-Do
I am yet to add another great tool Autopilot Branding from Michael Niehaus, which overcomes a few annoyances with Autopilot - such as the time zone issue. More on that later.
Happy Deploying Everyone! 😊
